Service Account It provides an identity for the processes that run in a Pod. Access to k8s cluster using kubectl command is authenticated by...
Service Account
It provides an identity for the processes that run in a Pod.
Access to k8s cluster using kubectl command is authenticated by the API server. The processes that are running inside the pod also contact the API server using the service account.
default service account
Whenever a namespace is created then a default service account is created along with the namespace.
kubectl create ns dev
kubectl get sa -n dev # you will find a default sa
kubectl describe sa default -n dev
kubectl get secret -n dev
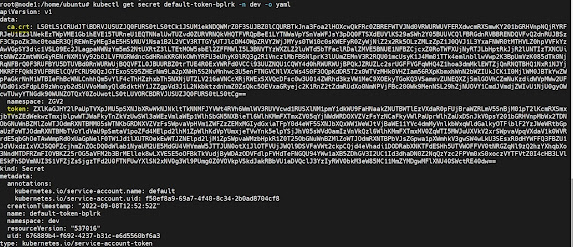
kubectl describe secret default-token-bplrk -n dev
kubectl get secret default-token-bplrk -n dev -o yaml
# Let's decode the namespace(ZGV2 in the above screenshot) it should be dev
echo ZGV2 | base64 -d
CA confirmation
If we decode ca.crt value and check /etc/kubernetes/ca.crt it should be same
token is encrypted jwt token it is passed to apiserver when sa communicate to apiserver.
Access API Server
kubectl config view # to find the cluster dns server
- consider cluster server is https://172.31.7.208:6443
curl https://172.31.7.208:6443/api --insecure
You will find that we are not able to access the api, so let's access it with the service account. Decode the token of dev namespace and run the below command
curl https://172.31.7.208:6443/api --insecure --header "Authorization: Bearer <<token decoded value >>
So it means the default service account can communicate to the API Server and the same service account is by default used with POD and that why the POD can communicate with API server







COMMENTS